Ransomware Attacks: Preparation is the Best Protection Part 2 –What to do After Attack
This article is a continuation of Part 1 of this series, which provides an overview of ransomware, why it should be a concern, and prevention techniques.
Unfortunately, engaging in preventative measures cannot always stop a cybersecurity attack. In the event of a ransomware infection, stay calm and weigh your options. Before making the decision to pay any kind of ransom (which the FBI and other leading security experts and organizations, e.g. Microsoft advise against), identify the version of ransomware that you’re dealing with.
Understanding the Ransomware That’s Attacking You
Try and determine how much information you are still able to access. Can you exit to your desktop? Can you open files and folders? There are two common types of ransomware attacks, screen-locking ransomware, and encryption-based ransomware, which function differently.
- Viruses That Imitate Ransomware – If you can navigate your system relatively freely, you’re likely encountering a fake pop-up attempting to imitate a ransomware attack in order to solicit money — in this case, you can simply exit, or force close the browser.
- Screen-Locking Ransomware – If you can’t navigate past the ransom note, you’re more than likely being attacked by screen-locking ransomware, which is typically considered a less serious virus.
- Encryption Based Ransomware – If you’re able to navigate applications and directories, but not documents and other file types, you’ve probably been attacked by encryption-based ransomware, which is a much more serious type of infection.
Knowing the type of ransomware you have been infected with will help determine the necessary steps that should be taken in order to attempt recovery. Since we all know that prevention is better than cure, it might be a good idea to invest in a VPN service (to compare various VPN services, check thevpnexperts.com) that could help encrypt your data making it more difficult for hackers to track you.
Steps to Perform When Infected
If you have been infected with ransomware, you need to respond and take immediate action to prevent the ransomware from spreading, as well as to get yourself back up and running.
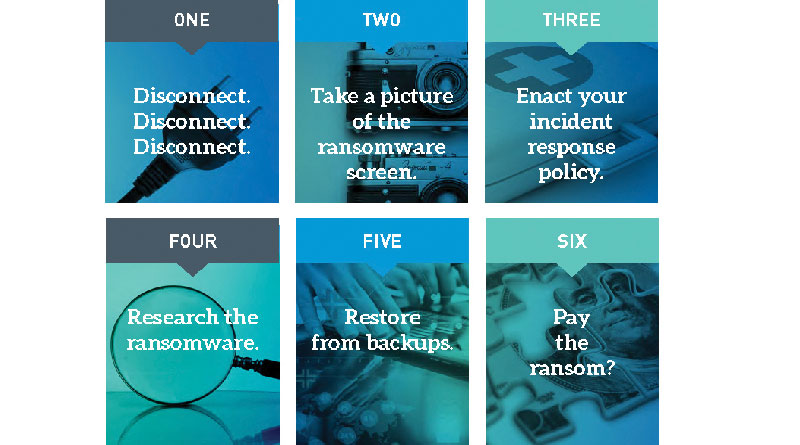
These steps include:
- Disconnect, disconnect, disconnect. Nothing is more important than trying to restrict the impact of the infection by disconnecting your device to prevent the malware from spreading. Unplug or disconnect from the network, wireless, file-syncing services (e.g. Google Drive, SyncToy, Box), and external devices (printers, phones, USB devices).
- Take a picture of the ransomware screen. Ransomware will be accompanied by a note that will identify the ransom, including the amount to be paid and where to send the payment. Take a picture so you have that information readily available to research the ransomware and to report the incident to the appropriate authorities.
- Enact your incident response policy. If you have one, now is the time to brush off that incident response policy. Follow the steps outlined in your incident response policy, to ensure that all of the right steps are taken, ultimately including notifying stakeholders in a timely manner. Note that depending on the information housed on the infected system(s), you may be required to report the incident as a breach based on your governing federal and state regulatory agencies’ respective breach notification laws.
- Research the ransomware. Depending on the ransomware, you may be able to recover your data using software available online or obtain a means to decrypt the files without having to pay the ransom. Tools such as Ransomware Identifier and ID Ransomware are available to allow you to upload encrypted files to determine what ransomware you were infected by and if there is a known way of decrypting the files. There may be a known way to decrypt the ransomware, such as the decryption code or a tool available to decrypt the files, such as those available through Kaspersky and No More Ransomware. As a general first step prior to trying to decrypt the files, it is best to involve forensics experts early in the process. Forensic experts can utilize their isolated laboratories to analyze and investigate various methods of trying to decrypt the infected system(s) as cybercriminals are aware of these tools as well and trying to de-encrypt the ransomware may further reduce your chances of recovering the system(s).
- Restore from backups. Depending on how frequently you backup your system and data, you may want to restore your systems from backups. Prior to doing that, you should ensure that you have the installation media and license keys that you’ll need in order to reinstall third-party software. Additionally, be aware that the ransomware could have been lingering for a while within your system, so your backups could be compromised as well. It is recommended to test the restore from the backup onto another machine (knowing that this machine could become encrypted as well), to allow you to still be able to decrypt your machine if you need to. If you determine that you are able to restore from the backup, you’ll need to fully restore your system first to ensure that the ransomware is gone. Modern Windows (Windows 7 or newer) operating systems allow you to do a “System Restore” when restarting your machine, or you can restore using the initial installation disk. Additionally, before restoring, you should run the antivirus software.
- Pay the ransom? As a last resort and if you have determined that you would lose too much critical information as a result of your system becoming corrupted, you may choose to pay the ransom. If the contact information is provided with how to contact the criminals responsible for the attack, as is commonly the case, reach out to them and negotiate the ransom. Before making any payment remember that ransomware is not being put out by the most ethical people, so you may be paying a ransom to get nothing in return. On the other hand, it wouldn’t be as profitable for cybercriminals if they got a reputation for not providing the decryption code. Once you do pay, it will spread across the Dark Web about your cooperation/willingness to pay, which may lead to your organization being further targeted. As such, before doing so, be prepared and ensure that you are in a better position to protect yourself and respond to the next version of ransomware.
Who to Contact if Infected
If you’ve encountered a ransomware attack, it’s important to contact your local authorities. You also want to make sure you inform either the Federal Bureau of Investigation’s local FBI office, or file a complaint online with the FBI’s Internet Crime Complaint Center. For help determining what type of ransomware you may have, technical support in executing the steps necessary to try and recover your information, or to perform a forensic analysis of the impact, reach out to a cybersecurity partner.
ABOUT WITHUMSMITH+BROWN, PC (WITHUM)
Withum provides clients in the hospitality, vacation ownership and other industries with assurance, accounting, tax compliance, advisory and cybersecurity services. For further information about Withum and the services they provide to the industry, contact Lena Combs (LCombs@withum.com) at (407) 849-1569 or visit www.withum.com.